Portfolio Details
Command-and-Control (C2) RAT
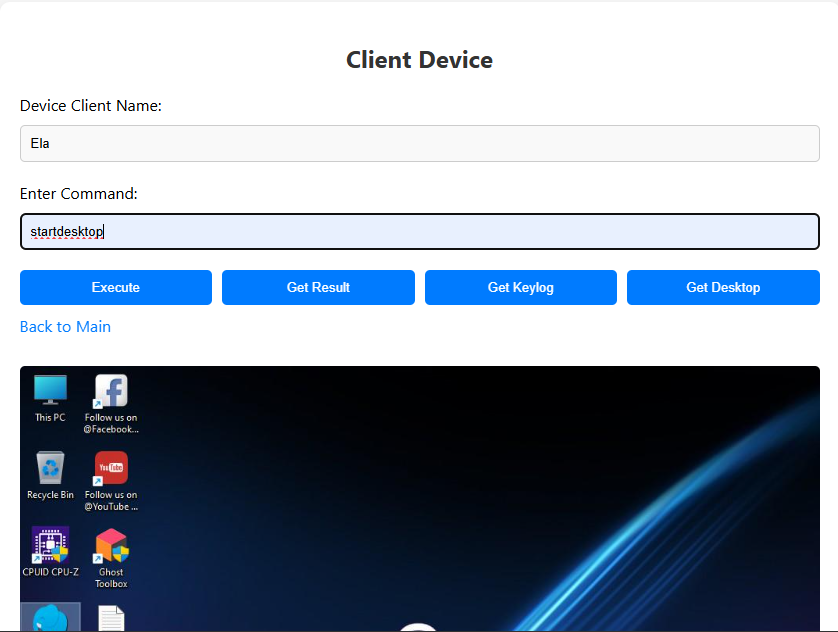
Client
Felix Eladi
Date
10 May, 2025
Category
Cybersecurity
This project is a C#-based Remote Access Tool (RAT) coupled with a custom PHP-powered Command-and-Control (C2) server. It uses a reverse connection model, where the agent (client) initiates communication with the server—allowing it to bypass NAT/firewall restrictions and maintain stealth. Built for internal lab use and red team simulations, it replicates advanced attacker behaviors while maintaining a secure and ethical testing environment.
Key Features
-
C# RAT Agent:
-
Reverse connection to the C2 server over WebSocket.
-
Remote command execution via shell.
-
File upload/download support.
-
Live screenshot capture.
-
Detailed system info collection (CPU, RAM, OS, IP, users, running processes).
-
Persistence via Windows registry/task scheduler.
-
Stealth execution with basic obfuscation.
-
-
PHP C2 Server:
-
Built using PHP with MySQL as the backend.
-
Web dashboard for viewing active agents, issuing commands, and viewing logs.
-
Processes incoming agent connections and queues responses.
-
Uses WebSocket/HTTPS for low-latency, encrypted communication.
-
-
Security & Stealth:
-
Communication is encrypted using TLS.
-
Session tokens for authentication.
-
Minimal process footprint and use of native Windows APIs for stealth.
-
Tech Stack
-
Agent: C# (.NET Framework 4.x / Core)
-
Server: PHP 8+, WebSocket Server (Ratchet or custom implementation)
-
Database: MySQL
-
Transport: Reverse WebSocket over HTTPS (TLS)
-
UI: HTML, CSS, JavaScript
Applications
-
Ethical hacking & red team simulations
-
Malware behavior analysis (in labs)
-
Blue team defense training (EDR, forensic analysis)
-
Educational demonstrations in secure cybersecurity environments
Challenges Solved
-
Reverse Connection: Bypasses inbound firewall rules, enabling remote access across NATed networks.
-
Agent Reliability: Added reconnection logic and queue buffering for unstable networks.
-
Obfuscation: String/function-level obfuscation to evade signature-based AV detection.
-
Authentication: Agent sessions are validated using per-device tokens and IP whitelisting.
Ethical Statement
This project is strictly for ethical use, educational demonstrations, and controlled lab simulations. It is never deployed in unauthorized environments. All testing is conducted in compliance with cybersecurity research standards.
Status: Active (Privately Hosted for Internal Use)
Source Code: Strictly confidential. Not publicly available. Access is limited to authorized personnel only.
Demo: Privately hosted on a secure internal server. Not accessible to the public. External access requires authentication and explicit authorization.
⚠️ Security Notice: This system is hosted in a restricted environment for research and simulation purposes only. Unauthorized access attempts are monitored and logged. Legal action will be pursued for misuse.
⚠️ Security Notice: This system is hosted in a restricted environment for research and simulation purposes only. Unauthorized access attempts are monitored and logged. Legal action will be pursued for misuse.
